Identity’s real problem isn’t tools. It’s the semi-async middle layer
Identity doesn’t need more dashboards, it needs fewer bottlenecks. Until we escape the semi-async middle, identity programs will keep seeing the risk they still can’t fix.

Table of Contents
Every year, identity gets more tools, more standards, more “platforms,” more pretty diagrams.
And yet, inside most enterprises, the lived reality of identity is still this: things take too long, break too often, and require way more human glue than anyone will admit on a panel.
I’ve come to believe the root cause is simple:
Identity work is stuck in a semi-async middle layer. Too slow for humans to feel interactive. Too fragile for automation. Too essential to ignore.
Welcome to the Identity Semi-Async Valley of Death—where most workflows live.
Here’s a ~180-second walkthrough of what I mean—and why this middle layer is where identity automation goes to die.
Synchronous, Asynchronous… and the Ugly Middle
In an ideal world, identity work sits at two ends of a spectrum:
- Synchronous and Interactive: real-time checks, immediate feedback, “I click a button and the system responds.”
- Fully asynchronous and delegated: You hand off a job and forget about it until a result shows up with logs, evidence, and a summary.
But most enterprises are stuck in the awkward third mode: Semi-Async.
Jobs sort of run in the background, sort of need watching, sort of require manual rescue. They take long enough to break your focus, but not long enough that you feel safe walking away. They’re automated in theory, but supervised in practice.
It’s the moment you trigger a workflow and hover over the screen, half-expecting it to fail. It’s automated in theory, but supervised in practice.
It’s increasingly visible at the industry level too — Gartner’s IVIP (Identity Visibility & Intelligence Platforms), the new category is an acknowledgment that organizations don’t even have real-time visibility into identity relationships, entitlements, and risks.
Here’s how the three zones show up in the real world.
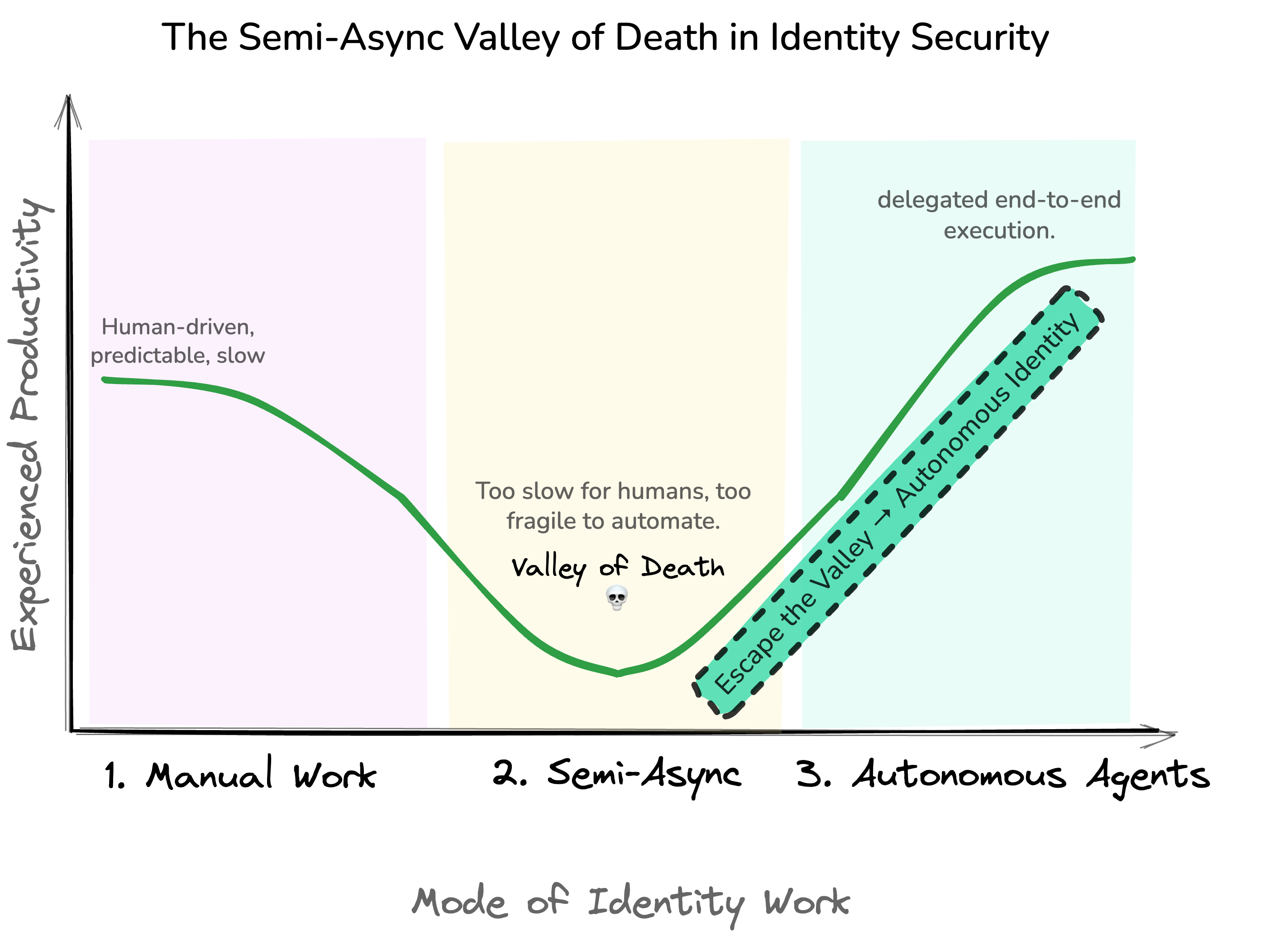
Zone 1: Manual, Slow, and Honest
At one end of the spectrum, you have purely manual identity work.
An analyst logs into three systems, finds the right record, makes the change, double-checks it, maybe grabs a screenshot “for the audit,” and moves on.
It’s slow. It doesn’t scale. It’s boring. But it has two huge advantages:
- A human brain is in the loop and understands context.
- When something weird happens, they can improvise.
Manual work is “honest misery”: painful, but predictable. You at least know who did what and why.
Zone 2: The Semi-Async Valley of Death
The middle zone—where most “modern” IAM claims to live—is what I call the Identity's Semi-Async Valley of Death. On slides, this is the promised land of automation: connectors, workflows, tickets, CSV jobs, RPA, recertification campaigns, all wired together into a neat diagram.
In production, it looks more like this:
- Connectors quietly fail and nobody notices until an audit.
- Workflows pause, waiting on an approval that sits in someone’s inbox for days.
- CSV imports drift out of alignment with the truth as data changes elsewhere.
- RPA bots break because a button moved or the app UI was redesigned.
- “Nightly jobs” become “sometime between midnight and whenever the batch server feels like it.”
The pattern is consistent: Too slow to feel interactive. Too brittle to trust. Too opaque to understand.
This is why I call it a valley. Productivity drops here. Security assurances quietly erode here. And the people who run identity programs end up babysitting the very automation that was supposed to free them.
Zone 3: Autonomous Agents as the Missing Layer
On the far right of that spectrum is where identity should be headed: delegation, not just assistance. Not another co-pilot that suggests policies. Not another connector marketplace. Not another workflow engine with nicer swimlanes. I mean autonomous identity agents that can safely and deterministically own an entire class of tasks.
You don’t ask them to “help with provisioning.” You tell them:
“Off-board this user everywhere they exist, capture the evidence, update governance, and surface only the edge cases that require a human.”
Concretely, that means agents that can:
- Operate across both APIs and UIs, so disconnected apps aren’t second-class citizens.
- Perform end-to-end deprovisioning: disable, remove, revoke, log, and prove it.
- Run continuous drift detection and remediation, not just raise tickets.
- Automate PAM rotation and check-in/check-out flows in a way humans can audit.
At that point, the main question for an identity team changes. It’s no longer:
“Did the workflow run?”
It becomes:
“Which responsibilities can we safely delegate to agents, and how do we monitor and govern them?”
That’s a very different conversation from “Do we have the right connector pack or did we configure the workflow?”
Why This Isn’t Just “We Need Better Tools”
We’ve spent years improving connectors, governance models, policy languages, federation standards, dashboards, and role mining. All of that matters. I’m not dismissing it.
But none of it fundamentally addresses this:
The majority of identity work is still trapped in a semi-async middle layer where humans are supervising automation instead of being freed by it.
That’s the real bottleneck. As long as identity tasks sit there—half-automated, half-manual, half-trusted—the experience will stay the same: slow, noisy, and surprisingly manual under the surface.
The real shift isn’t “more tools.” It’s moving the work itself:
- Some of it back into tight, synchronous, human-driven loops where context matters.
- Much more of it forward into fully autonomous execution, where agents own the workflow from trigger to evidence.
Conclusion
Identity doesn’t have a tooling problem. It has a work placement problem. Keep high-context tasks synchronous and human. Push the repeatable execution fully autonomous and auditable. But until we evacuate the semi-async middle, identity will keep looking modern—while operating like a helpdesk with better branding.
Close Your IAM Blast Radius.
See how Redblock replaces ticket-driven identity execution with continuous lifecycle enforcement across your application estate.